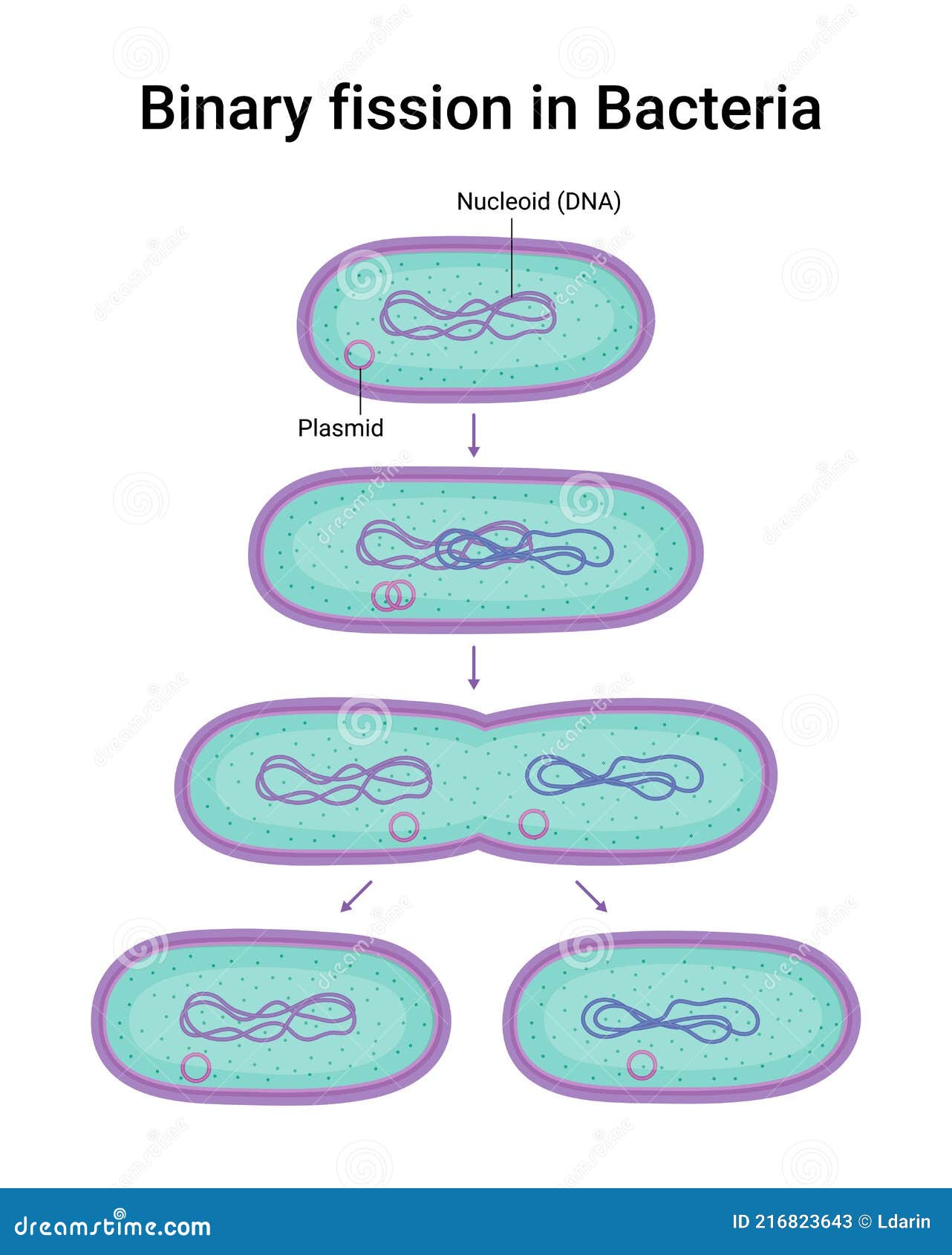
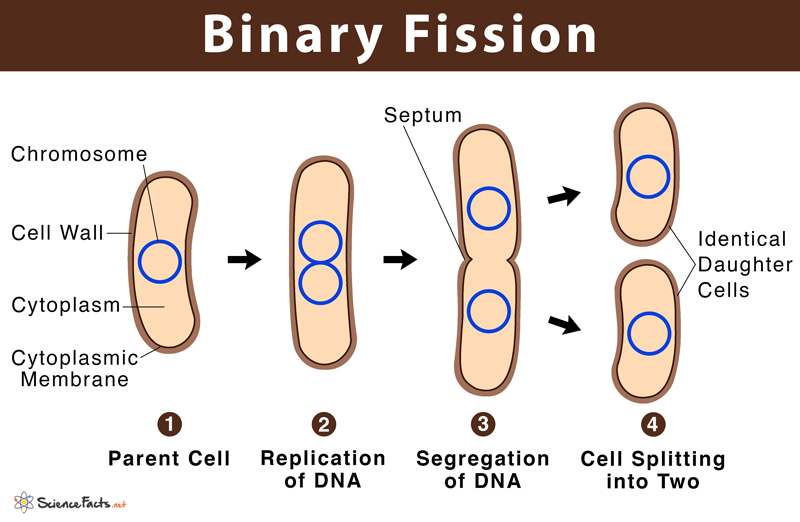
Fission Asexual Reproduction 2026 Storage Full Media Free Link
Claim Your Access fission asexual reproduction superior digital media. On the house on our content platform. Get lost in in a great variety of themed playlists available in best resolution, perfect for top-tier watching buffs. With up-to-date media, you’ll always stay current. Witness fission asexual reproduction expertly chosen streaming in incredible detail for a remarkably compelling viewing. Participate in our community today to get access to exclusive premium content with completely free, no need to subscribe. Enjoy regular updates and investigate a universe of bespoke user media engineered for top-tier media fans. Be sure not to miss special videos—save it to your device instantly! Explore the pinnacle of fission asexual reproduction uncommon filmmaker media with flawless imaging and members-only picks.
What is cyber threat intelligence Their main job is to turn a vast amounts of the data into useful insights that can help protect an organization. Threat intelligence refers to the collection, processing, and analysis of data to understand a threat actor’s motives, targets, and attack methods
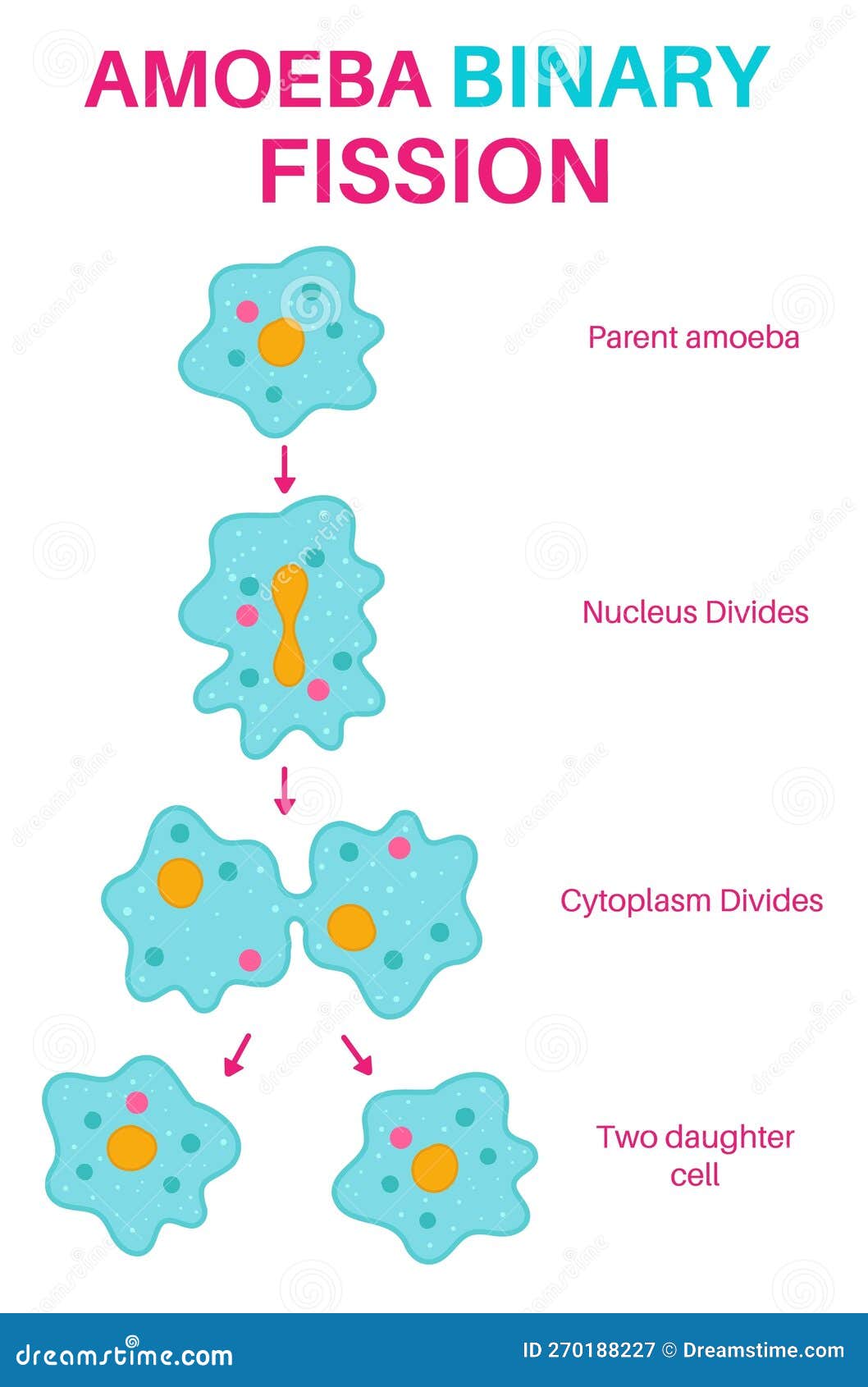
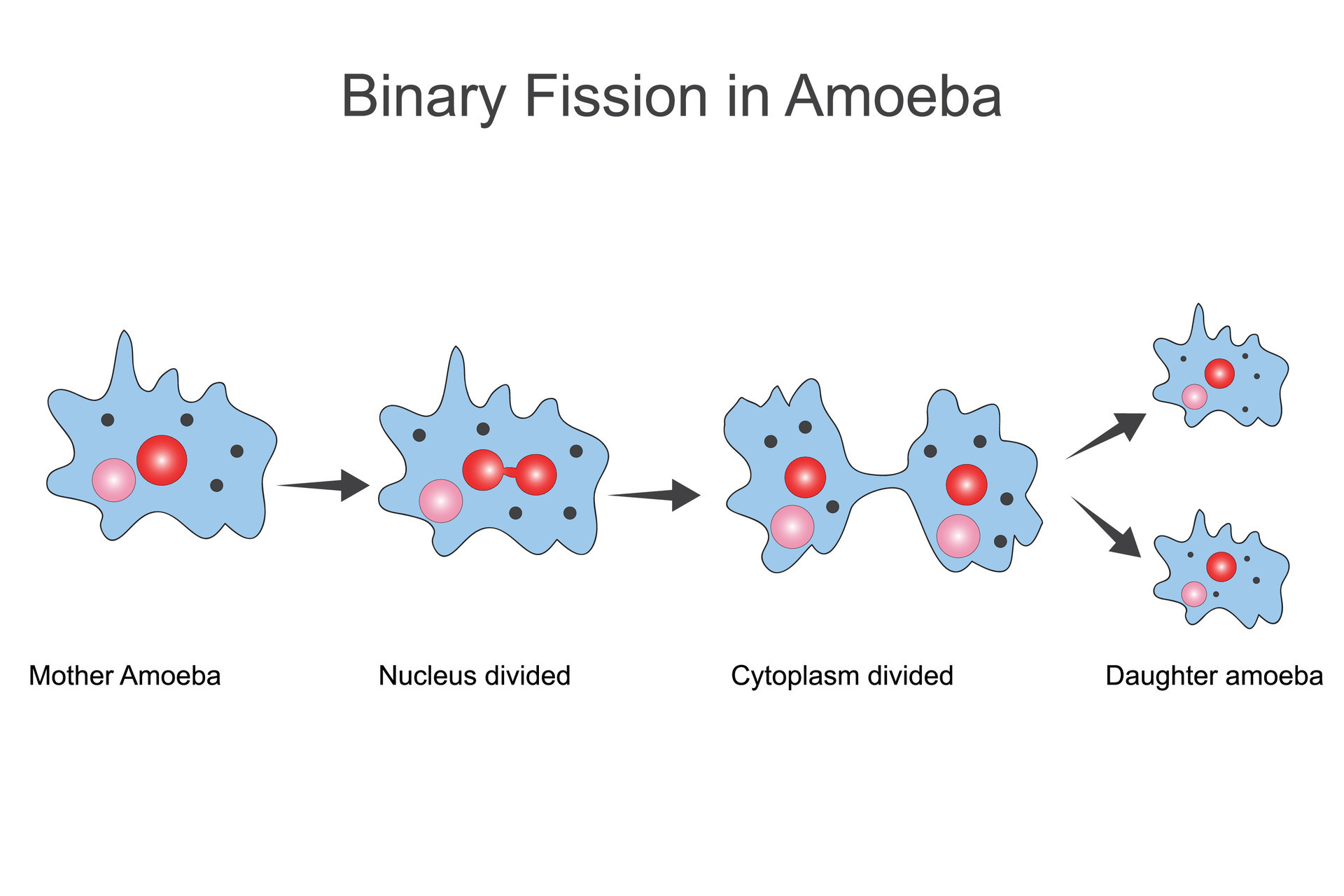
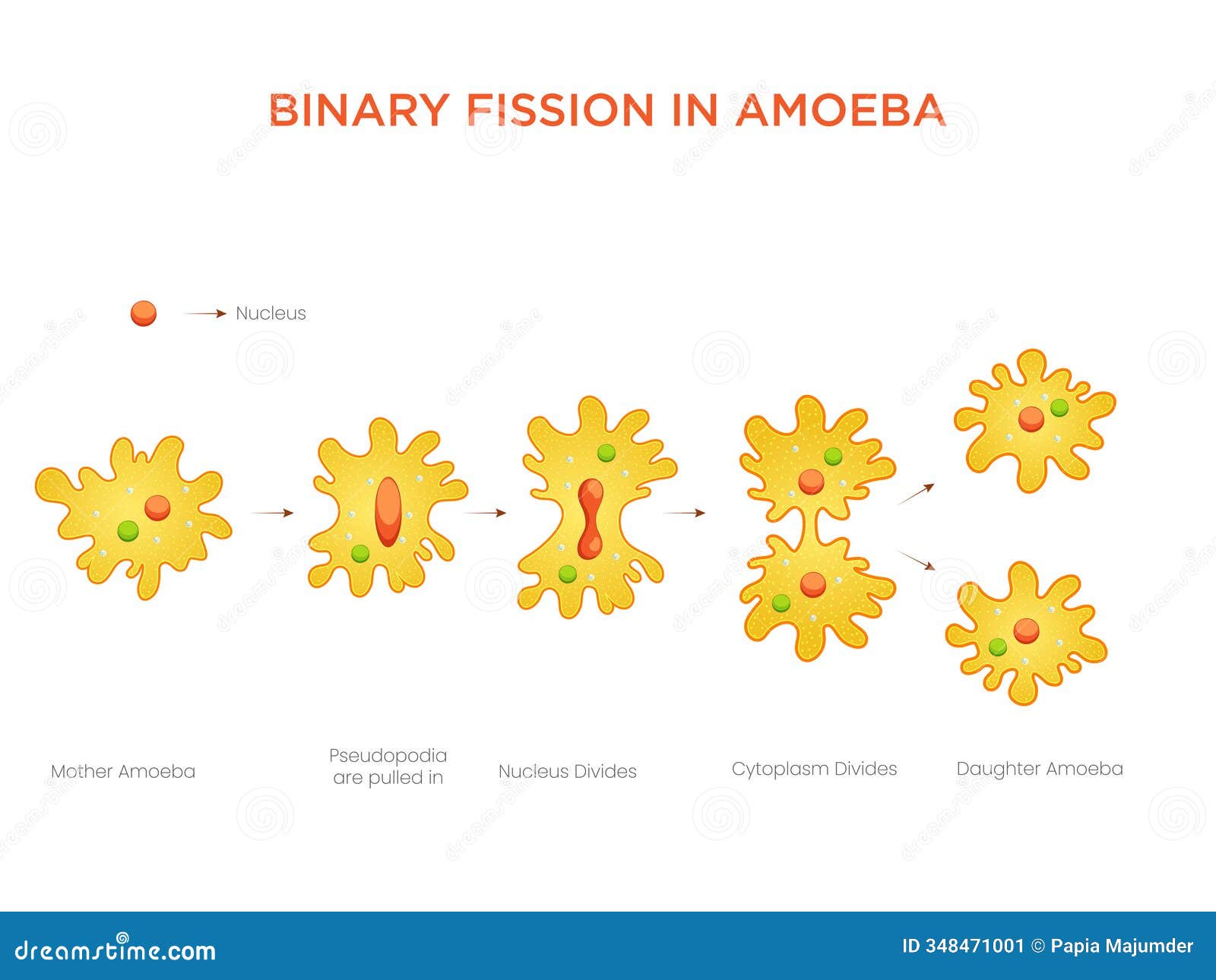
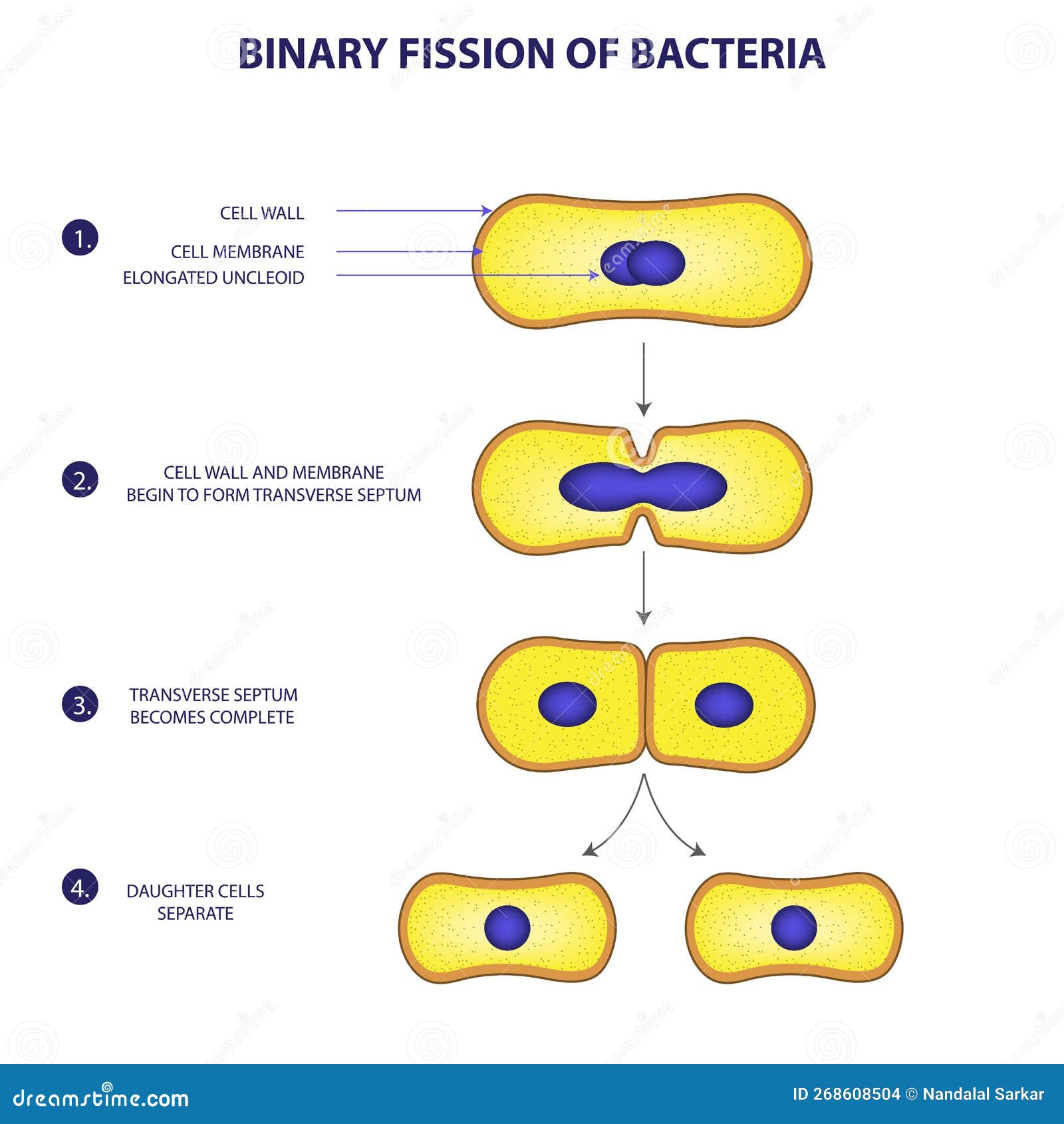
Premium Vector | Binary fission asexual reproduction of some
Threat intelligence—also called cyberthreat intelligence (cti) or threat intel—is detailed, actionable information about cybersecurity threats The cyber threat intelligence analyst is a security expert who specializes in the monitoring and analyzing the information about a external cyber threats Threat intelligence helps security teams take a more proactive approach to detecting, mitigating and preventing cyberattacks.
Threat intelligence, or cyber threat intelligence, is security data and information an organization gathers and analyzes to understand the threat landscape.
Cyber threat intelligence (cti) is a subfield of cybersecurity that focuses on the structured collection, analysis, and dissemination of data regarding potential or existing cyber threats [1][2] it provides organizations with the insights necessary to anticipate, prevent, and respond to cyberattacks by understanding the behavior of threat. The threat intelligence lifecycle, part of the broader cyber threat intelligence definition, comprises the following six interconnected phases This is the initial phase where security teams collaborate with business stakeholders and decide on the threat intelligence program’s goals
It involves outlining the crucial data and assets that require protection Cyber threat intelligence (cti) is the process of collecting, analyzing, and applying data on cyber threats, adversaries, and attack methodologies to enhance an organization's security posture It involves taking raw threat data from various sources and transforming it into actionable insights that enable organizations to anticipate, detect, and respond to cyber risks Introduction threat intelligence is an elusive concept
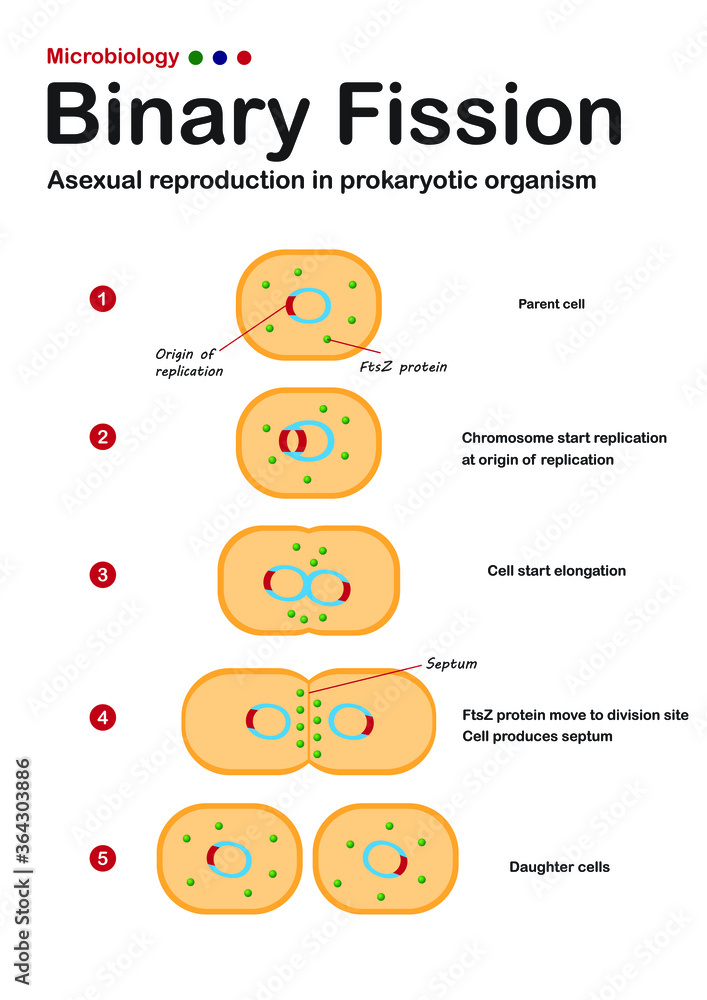
As a result, the scope of this paper is limited to an introduction of the key concepts and principles of threat intelligence, explaining the role it plays within network defence.
![[Biology] Fission in Asexual reproduction - Types, Examples (& images)](https://d1avenlh0i1xmr.cloudfront.net/ec7598a5-a36d-471d-a8ac-e240524055b8/multiple-fission---teachoo.jpg)